Interface Gallery
Screenshots of the RED Team Toolkit interfaces
LOGIN_INTERFACE
Secure authentication terminal
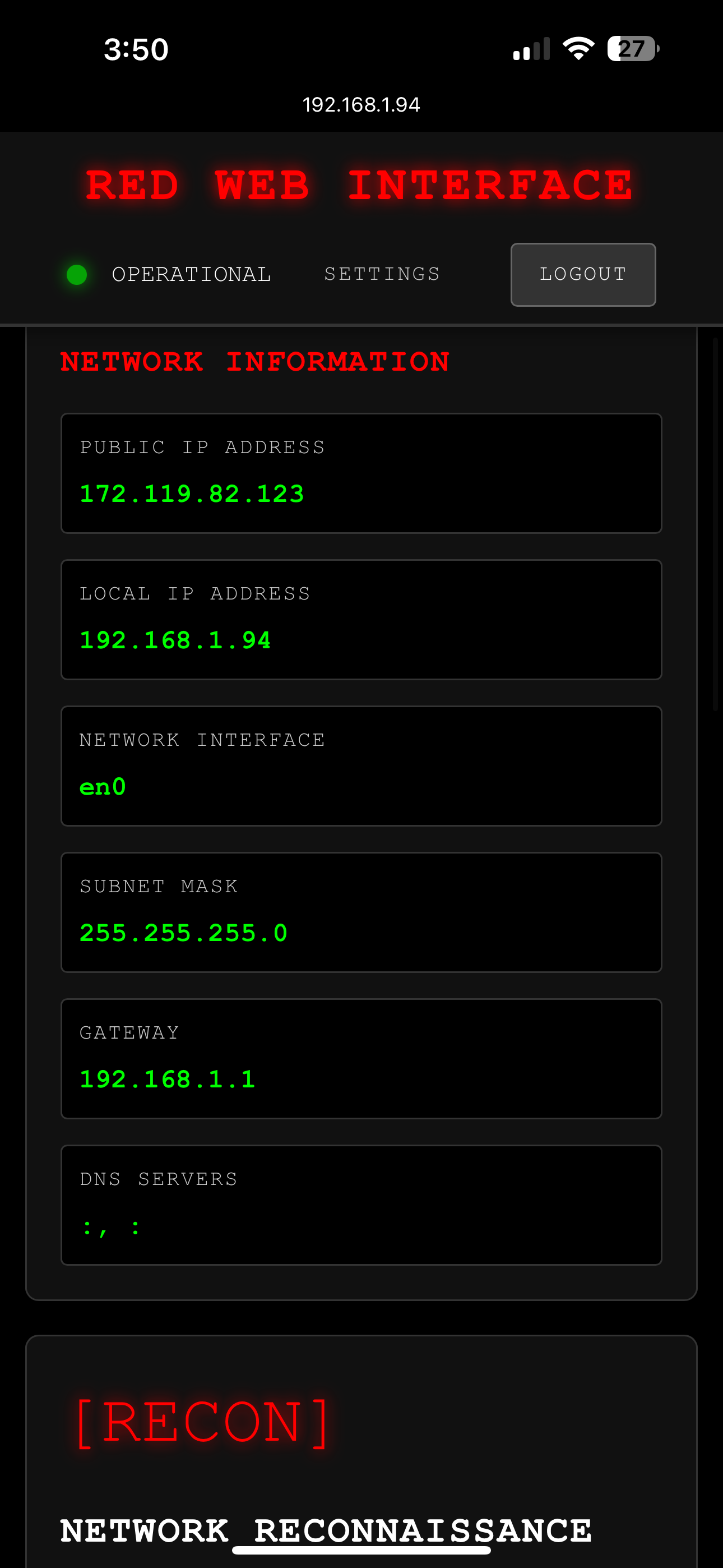
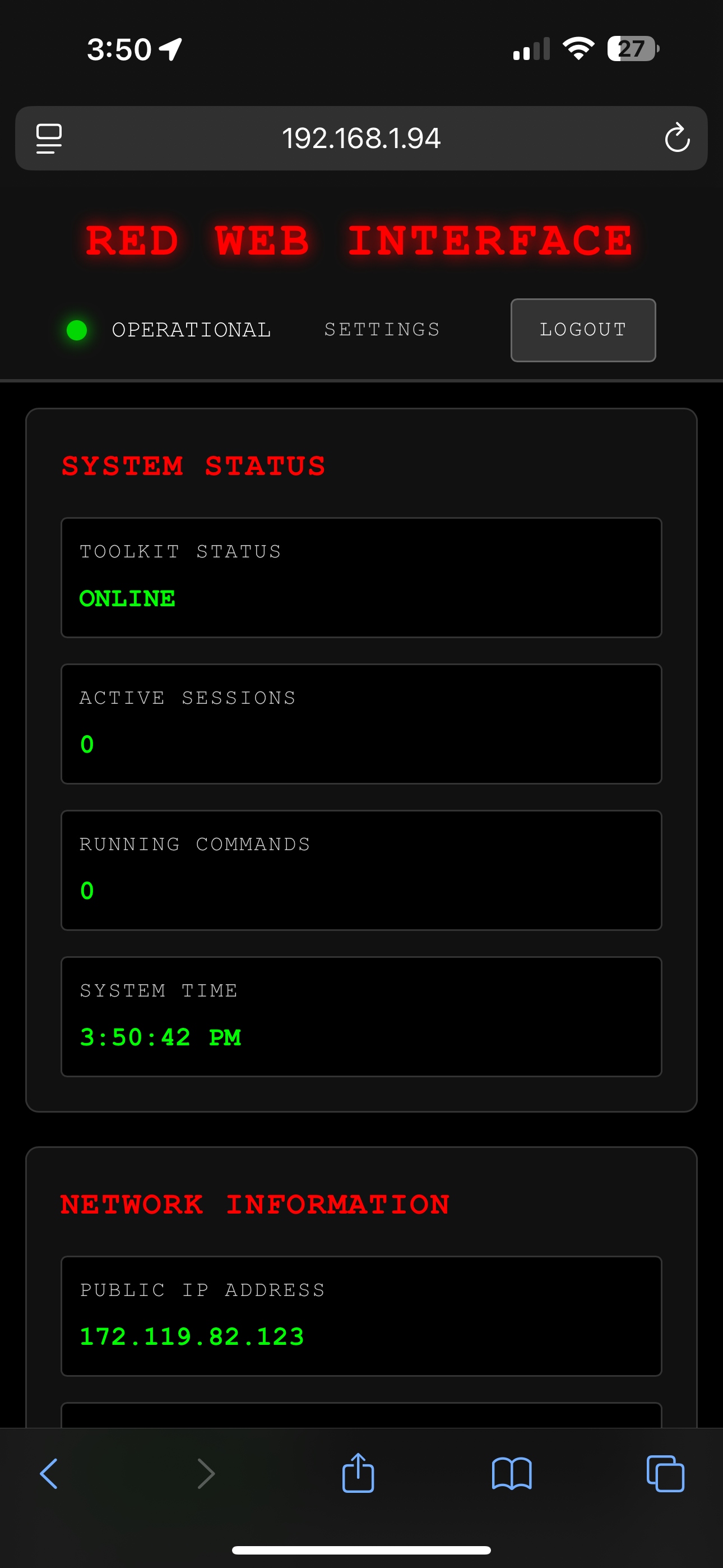
DASHBOARD
Control panel access
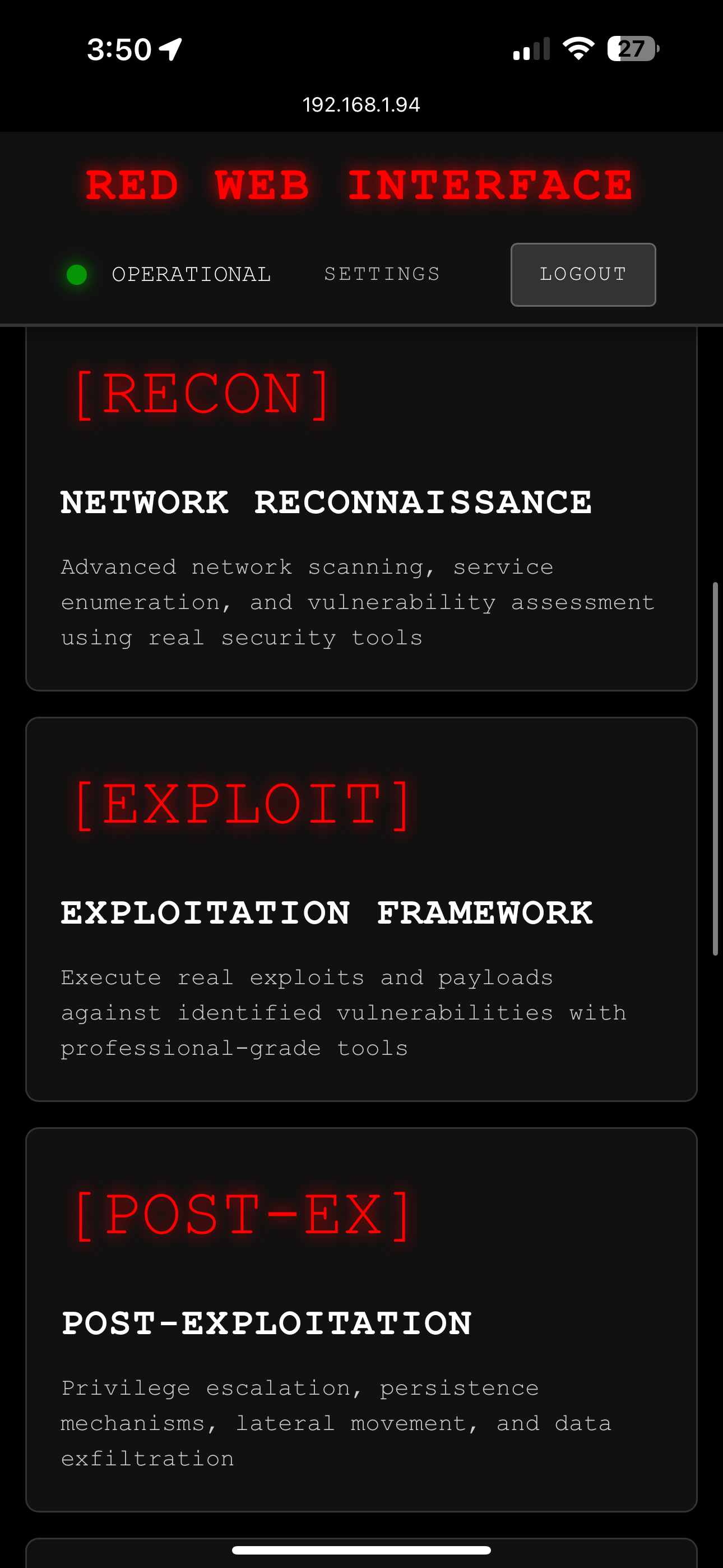
ATTACK_MODULES
Toolkit modules
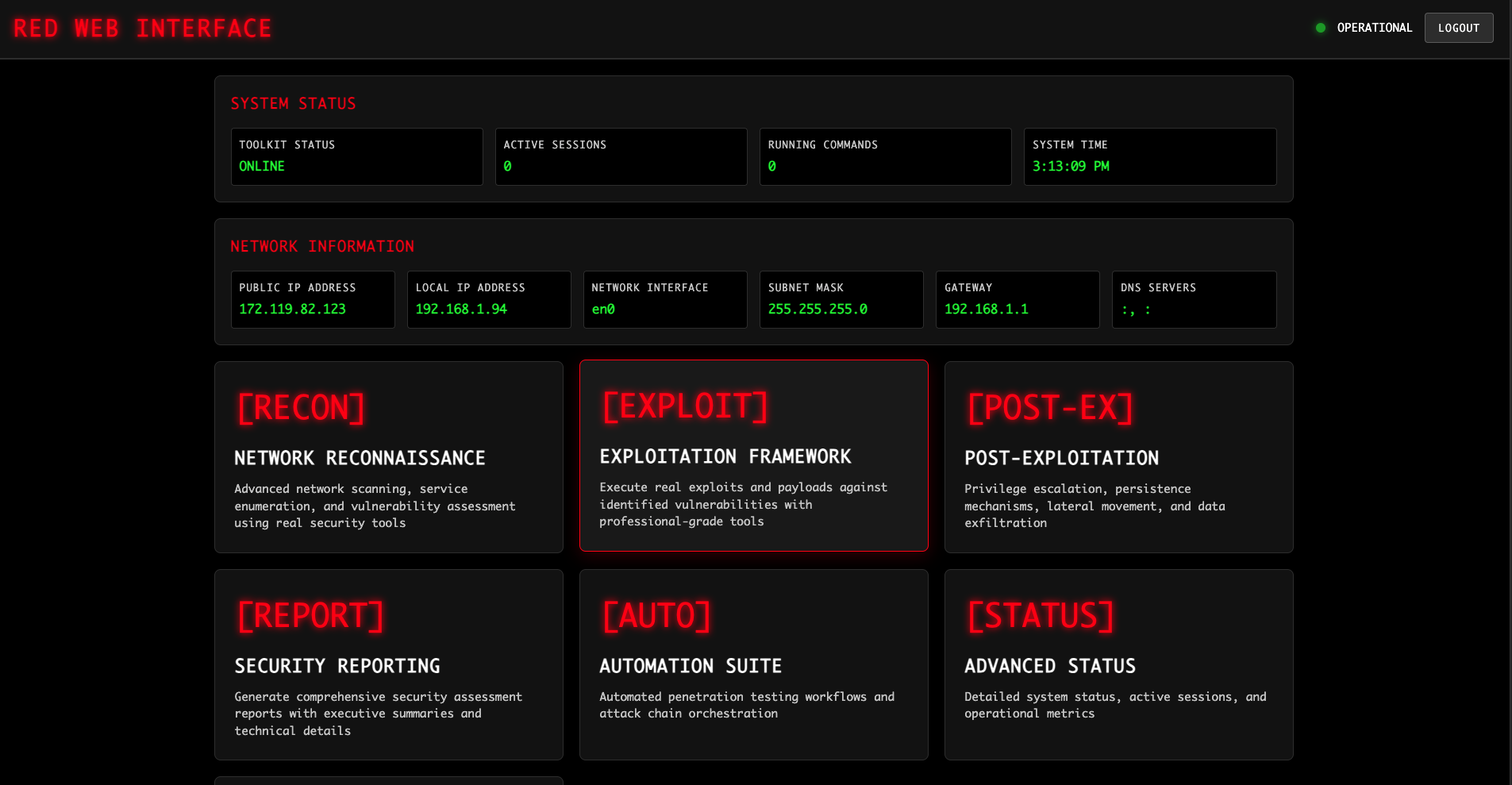
MAIN_INTERFACE
Full desktop toolkit
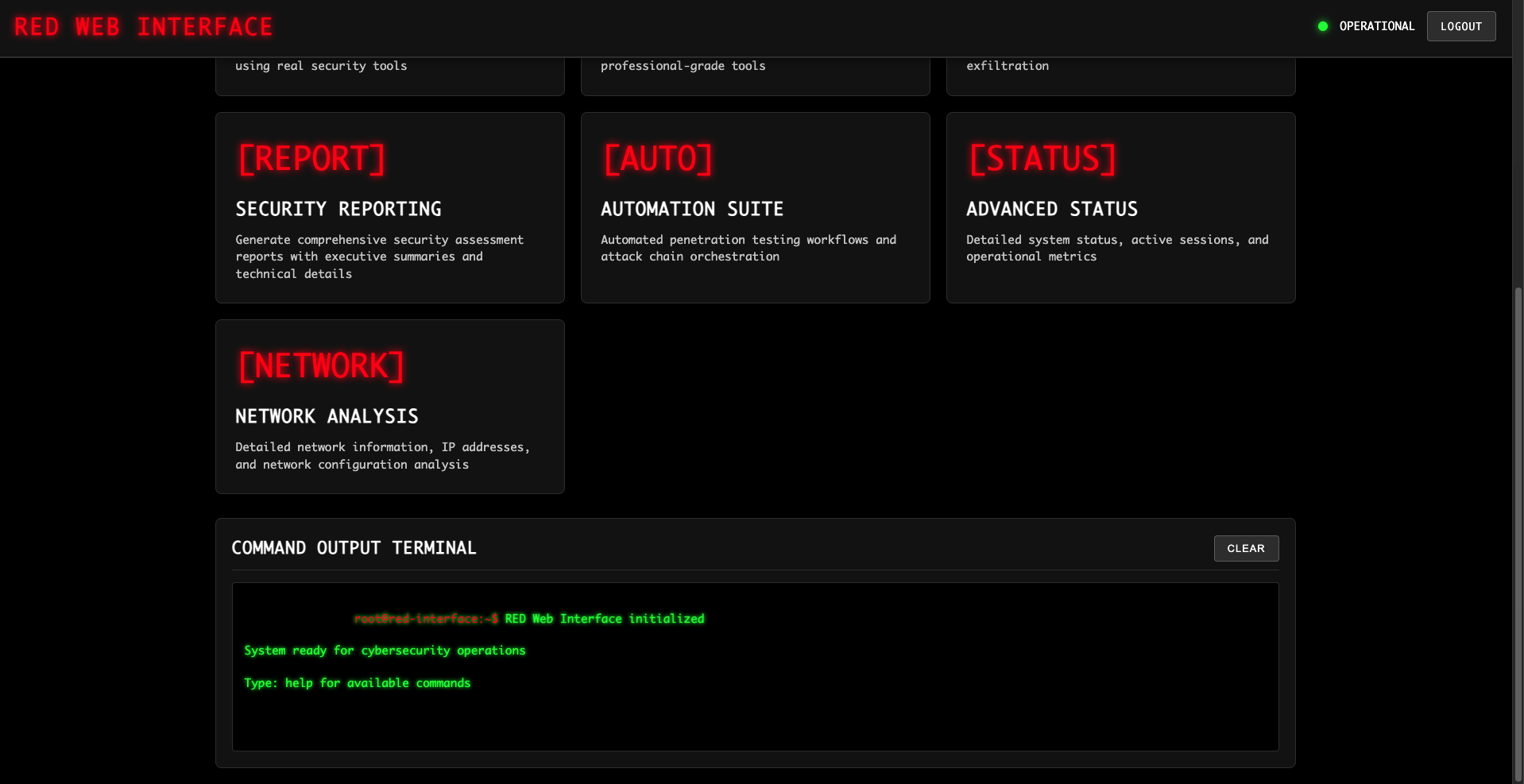
MODULE_SELECTION
Attack module interface
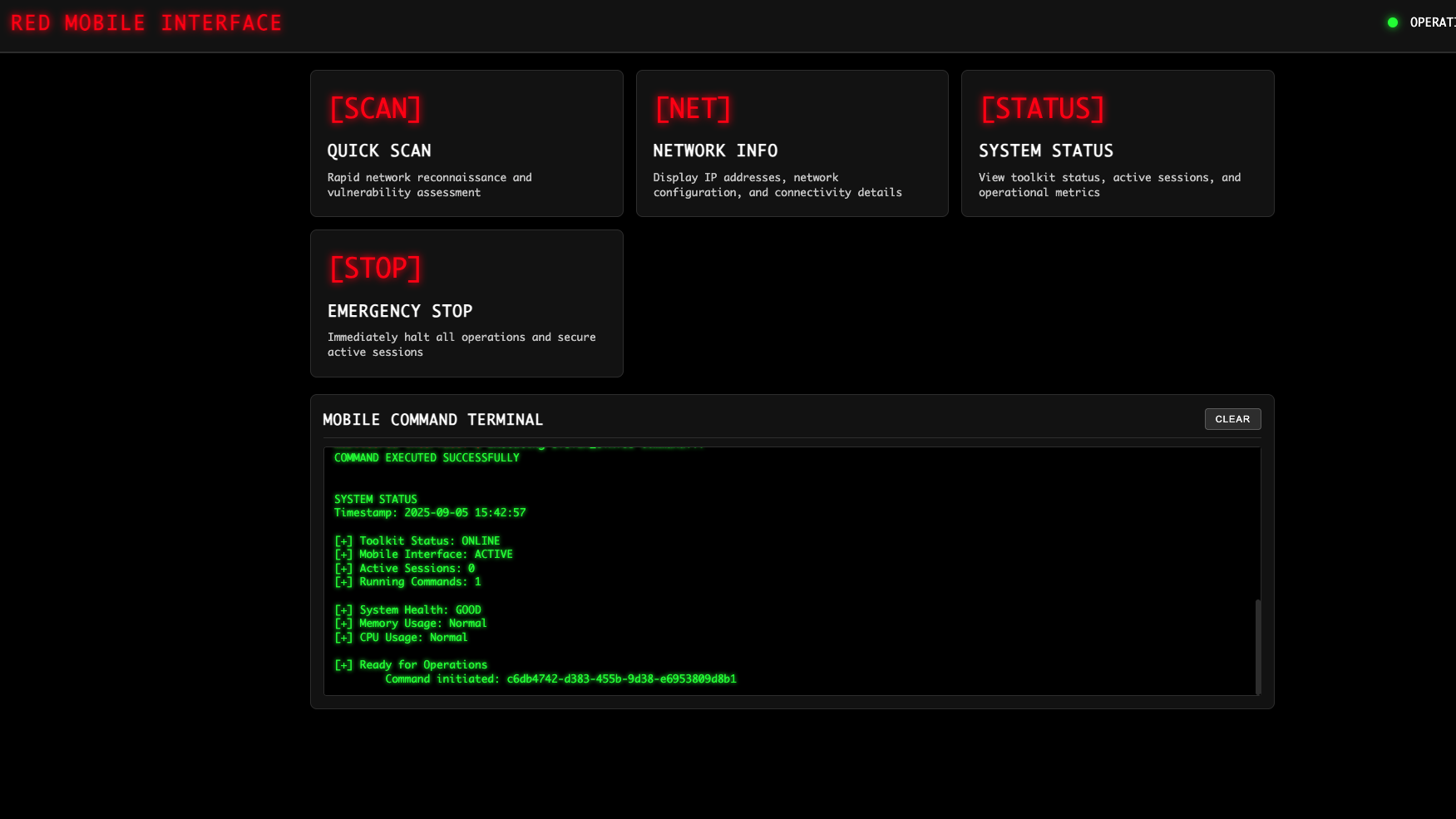
WEB_DASHBOARD
Web control panel
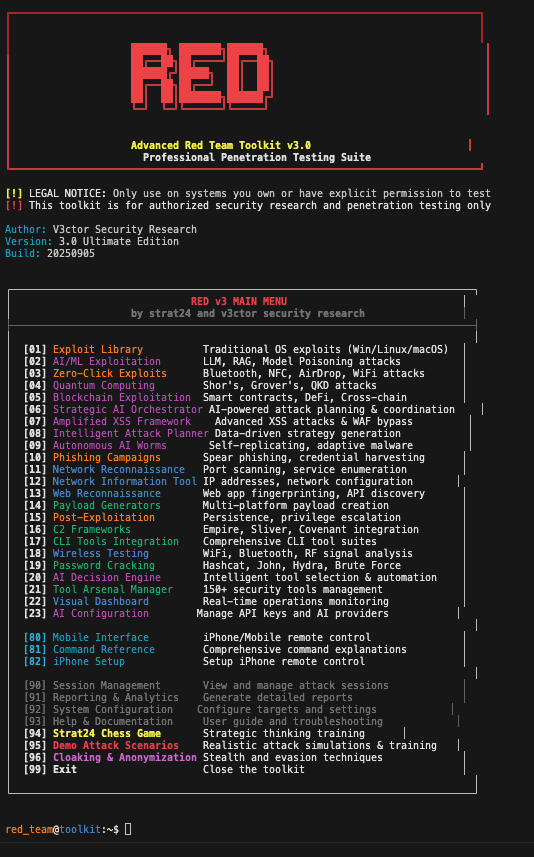
CLI_INTERFACE
Command-line terminal